THM/AOC25 : Road To Side Quest 1
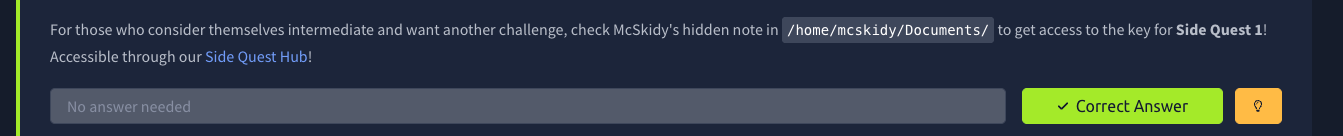
di bagian bawah dari room pertama AOC2025 ada challenge tambahan untuk memasuki Side Quest 1
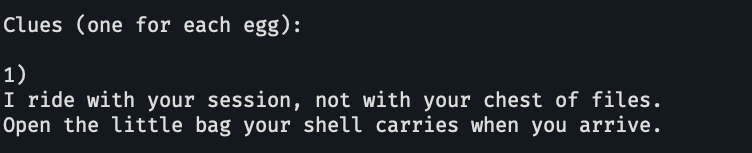
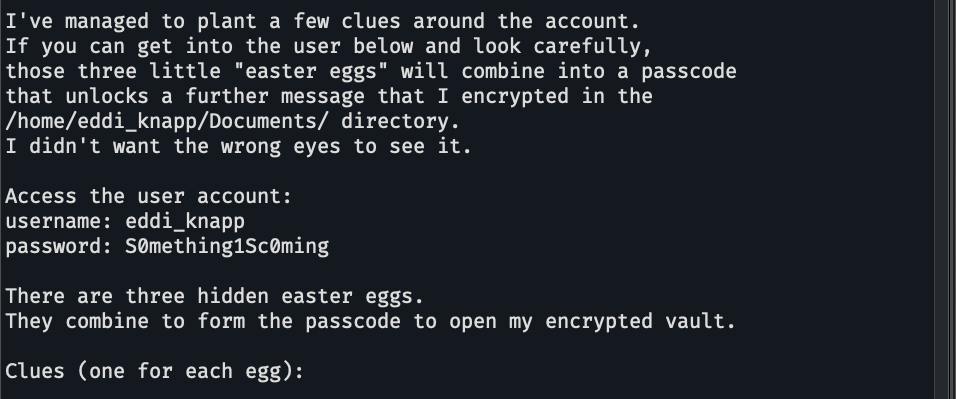
Sesuatu yang selalu bersama di session, bukan file. aku duga itu adalah Environment Variables , di ubuntu bisa dicetak dengan printenv.
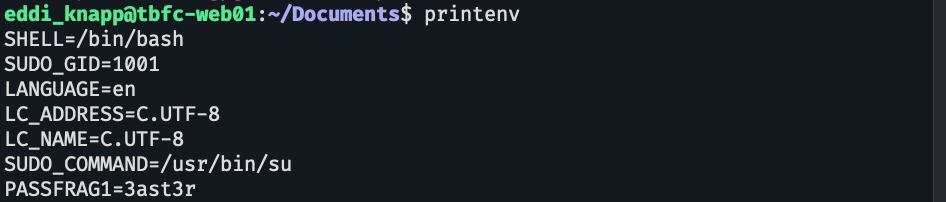
ketemu, oke lanjut.
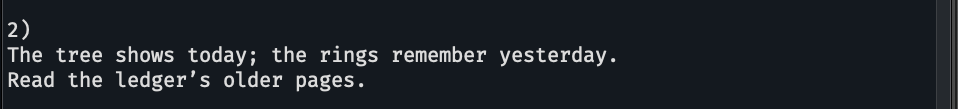
the tree shows; setelah membaca ini aku jalankan tree -a untuk menampilkan tree dari home directory sekarang dan menemukan file tersembunyi berikut.

setelah di-cat malah dapat PASSFRAG ke 3 😭
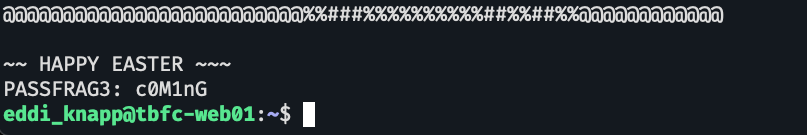
setelah dapat kedua PASSFRAG itu sebenarnya bisa kita tebak tebak PASSFRAG keduanya tapi kita lanjut aja deh carinya
di CLUE kedua ada 3 kata kunci ternyata yaitu tree-yesterday-older kata kata ini bersinggungan dengan git version control. tadi ketika melakukan tree -a dapat dilihat juga ada folder .secret_git

setelah kita masuk dan lakukan git log untuk melihat riwayat commit, kita mendapatkan clue lagi
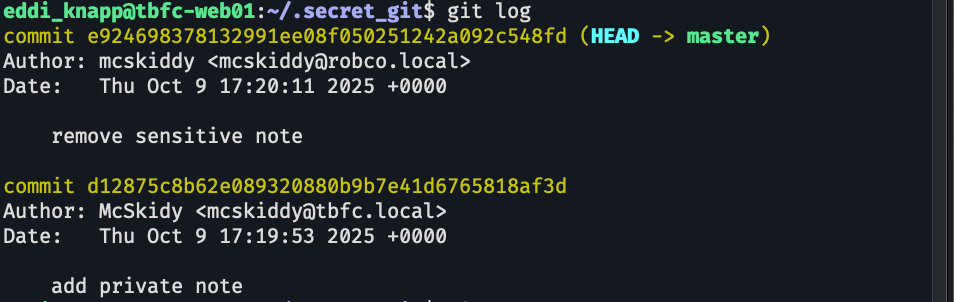
yak berarti disini pernah ada private note, kita hanya perlu melakukan checkout ke commit kemarin (yesterday) sebelum private notenya dihapus dengan menggunakan git checkout <hash commitnya>
kemudian kita ls , dan benar saja ada sebuah file txt disana, di dalamnya ada PASSFRAG kedua
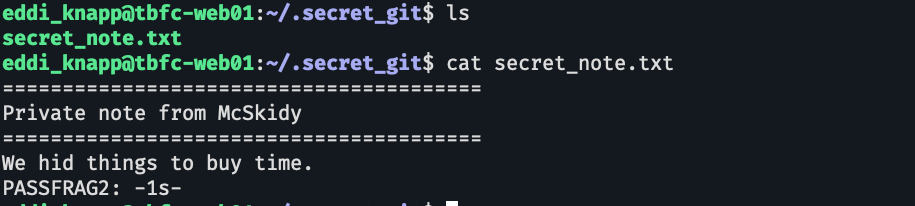
btw ini clue ketiganya (passfragnya udah ketemu tadi)
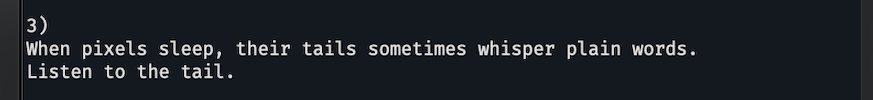
oke jadi kita udah dapat keynya yaitu 3ast3r-1s-c0M1nG tinggal kita gunakan untuk membuka enkripsi filenya
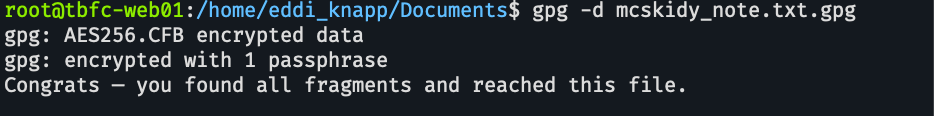
root@tbfc-web01:/home/eddi_knapp/Documents$ gpg -d mcskidy_note.txt.gpg
gpg: AES256.CFB encrypted data
gpg: encrypted with 1 passphrase
Congrats — you found all fragments and reached this file.
Below is the list that should be live on the site. If you replace the contents of
/home/socmas/2025/wishlist.txt with this exact list (one item per line, no numbering),
the site will recognise it and the takeover glitching will stop. Do it — it will save the site.
Hardware security keys (YubiKey or similar)
Commercial password manager subscriptions (team seats)
Endpoint detection & response (EDR) licenses
Secure remote access appliances (jump boxes)
Cloud workload scanning credits (container/image scanning)
Threat intelligence feed subscription
Secure code review / SAST tool access
Dedicated secure test lab VM pool
Incident response runbook templates and playbooks
Electronic safe drive with encrypted backups
A final note — I don't know exactly where they have me, but there are *lots* of eggs
and I can smell chocolate in the air. Something big is coming. — McSkidy
---
When the wishlist is corrected, the site will show a block of ciphertext. This ciphertext can be decrypted with the following unlock key:
UNLOCK_KEY: 91J6X7R4FQ9TQPM9JX2Q9X2Z
To decode the ciphertext, use OpenSSL. For instance, if you copied the ciphertext into a file /tmp/website_output.txt you could decode using the following command:
cat > /tmp/website_output.txt
openssl enc -d -aes-256-cbc -pbkdf2 -iter 200000 -salt -base64 -in /tmp/website_output.txt -out /tmp/decoded_message.txt -pass pass:'91J6X7R4FQ9TQPM9JX2Q9X2Z'
cat /tmp/decoded_message.txt
Sorry to be so convoluted, I couldn't risk making this easy while King Malhare watches. — McSkidy
root@tbfc-web01:~$ cat decoded_message.txt
Well done — the glitch is fixed. Amazing job going the extra mile and saving the site. Take this flag THM{w3lcome_2_A0c_2025}
NEXT STEP:
If you fancy something a little...spicier....use the FLAG you just obtained as the passphrase to unlock:
/home/eddi_knapp/.secret/dir
That hidden directory has been archived and encrypted with the FLAG.
Inside it you'll find the sidequest key.
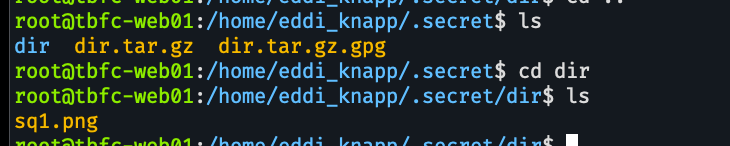

itu imagenya, selesai...
sekarang baru masuk ke challengenya (aku cuma bisa dapat 1 flag di side quest 1 jadi ga sampe selesai, hehe )